How to Enabling SMB Signing
Server Message Block (SMB) signing helps organizations confirm the origin and authenticity of network data traffic. It also helps mitigate threats like man-in-the-middle attacks.
Signing can be enabled on both SMB1 clients and servers via Group Policy or the registry. However, enabling signing on both sides can cause performance degradation.
Server Message Block (SMB) is a common file-sharing protocol used in Windows environments. While convenient, SMB traffic can be vulnerable to eavesdropping and man-in-the-middle attacks. Enabling SMB signing enhances security by adding digital signatures to SMB packets, ensuring data integrity and authenticity. This guide will cover the process of enabling SMB signing on both Windows servers and clients in various scenarios.
Understanding SMB Signing:
There are two levels of SMB signing:
- SMB Signing: This ensures data integrity by signing SMB packets, preventing attackers from modifying them in transit.
- SMB Encryption: This adds another layer of security by encrypting the entire SMB packet, protecting data confidentiality in addition to integrity.
Enabling SMB Signing on Windows Servers:
1. Group Policy Editor (GPO):
- This approach is ideal for managing signing across multiple servers in a domain environment.
- Open Group Policy Management Console (GPMC).
- Create or edit a GPO that applies to the target servers.
- Navigate to Computer Configuration > Administrative Templates > Network > Lan Manager Authentication Level.
- Set the policy to “Signing required (server)”.
- This enforces SMB signing for all inbound connections.
2. Local Security Policy:
- This method applies to individual servers not managed by GPO.
- Open Local Security Policy (secpol.msc).
- Go to Local Policies > Security Options.
- Find “Network security: LAN Manager authentication level” and set it to “Signing required (server)”.
- Apply the changes.
3. Registry Editor:
- Advanced users can use the registry for finer control.
- Open Registry Editor (regedit.msc).
- Navigate to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters. - Create a DWORD value named “RequireSigning” and set its value to 1 (enable signing).
- Restart the server for changes to take effect.
Enabling SMB Signing on Windows Clients:
1. Local Security Policy:
- Follow the same steps as for servers, but navigate to “Computer Configuration” instead.
- Set the “Network security: LAN Manager authentication level” to “Signing required (client)”.
- This enforces signing for all outbound connections.
2. Group Policy Editor (GPO):
- Similar to servers, configure the same policy for client computers in a domain environment.
3. Registry Editor:
- Follow the same steps as for servers, but navigate to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsainstead. - Create a DWORD value named “LMCompatibilityLevel” and set its value to 2 (enables signing).
- Restart the client.
Enabling SMB Encryption:
- SMB encryption requires additional configuration on both servers and clients.
- Servers need to have Schannel (TLS/SSL) certificates installed and configured.
- Clients need to trust the server’s certificate and have TLS/SSL enabled.
- Consult the official Microsoft documentation for detailed instructions on enabling SMB encryption.
Additional Considerations:
- Enabling SMB signing and encryption can impact performance, especially on older systems.
- Test thoroughly in a non-production environment before deploying changes.
- Consider the impact on compatibility with older clients or applications.
- Use strong cryptographic algorithms and secure key management practices.
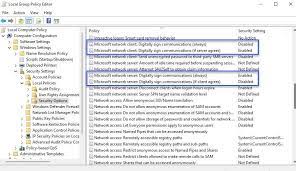
Group Policy
The Server Message Block (SMB) protocol is used for file sharing between computers and devices. SMB signing allows you to digitally sign the SMB communications so that tampering is detectable. The security signature is added in the form of an MD5 hash to each SMB packet.
This setting can be enabled via Group Policy; it is available in the Computer Configuration/Windows Settings/Security Settings/Local Policies/Security Options/Microsoft network client: Digitally sign communications policy. The default value is Enabled.
It’s worth noting that disabling the requirement for SMB signing on domain controllers can significantly increase SMB performance, but it exposes Group Policy to tampering and man-in-the-middle attacks. This is a risk that’s not worth taking.
You should also be sure that SMB ports 445 and 139 are only opened to trusted networks, as leaving them exposed to the Internet poses a serious security risk. In addition, you should also consider enabling encryption on your SMB shares to further enhance the security of your data.
Registry
SMB signing is an optional feature of the Server Message Block (SMB) file protocol that enables communication between network devices to be digitally signed at the packet level. This helps to prevent tampering of SMB packets and man in the middle attacks.
Disabling SMB signing for your network is a serious security risk. It can allow Rainbow table attacks to be used against your network to brute force or attempt NTLM relay attack and increase privileges across your network.
To avoid this risk, consider enabling SMB signing for your network by using either Group Policy or the Registry. The Registry setting for SMB signing is stored in HKEY_LOCAL_MACHINESystemCurrentControlSetServicesLanmanServerParameters on the client and in HKEY_LOCAL_MACHINESystemCurrentControlSetServicesLanmanWorkStationParameters on the server; you can specify whether signing should be required or not by setting values in these keys. However, requiring signing for your network might negatively impact performance and may affect older clients on your network that do not support it.
Clients
SMB signing (or security signatures) is a feature in Windows that prevents anyone from tampering with data during communication. It does this by adding a hash of the data inside the signature field in the SMB header. This ensures the sender and recipient of the message are who they say they are.
It can also help to slow down rainbow table attacks, where attackers try thousands of passwords per second to gain access to a system. This setting is only available on a newer version of Windows, however.
The other two policies are aimed at SMB servers, or Windows systems that host files and printers for communications over smb to clients within the network. When enabled, it will prevent a client from connecting to an SMB server if it does not support signing. This can cause a performance hit as SMB packet signing requires a hash to be added to each message.
Servers
SMB signing is supported in all versions of Windows except SMB1. When enabled on both the client and server the communications between the machines are signed at the packet level. This allows the receiver to verify the point of origin and authenticity of the data, and it prevents man in the middle attacks.
Signing also adds a security layer in that the signature is based on a hash of the message, so that if the hash changes during transmission the server will detect this and refuse to communicate with the client. This does however reduce performance slightly since each packet has to be verified.
By enabling SMB signing via GPO your network will be more secure, have improved performance and will be in compliance with many industry standards. To find out if you have any of these Medium risk vulnerabilities in your environment check out be SECURE, our vulnerability scanner can scan tens of thousands of IPs in large distributed networks and generate remediation tickets automatically.


