How to Enable TLS 1.2 on Your Android Phone
If you’re wondering how to enable TLS 1.2 on your Android phone, keep reading. There are a few things you need to know before you begin. First, you need to check the operating system status. Next, you need to enable TLS 1.2 in your operating system settings. Afterward, check the status of your internet browser. Make sure that the latter is enabled, or else you’ll be unable to browse websites securely.
According to Google Play Services, TLS 1.2 support is not enabled by default in Android 4.4. To enable it, you must make a few modifications to your FileTransfer app. However, be aware that enabling TLS may conflict with other certificates and may have unintended consequences. Additionally, some vendors have removed TLS 1.2 support altogether, so you might be faced with an unstable connection Google.
Android 4.4 users can continue to use RingCentral Phone versions 8.1 and higher. However, if your device is older than two years, you will be required to upgrade your browser. This is because older versions of RingCentral are not compatible with TLS 1.1/1.2. Also, if you are using an older version of Android, you will not be able to use any of your applications. TLS 1.1/1.2 is not supported by Android 4.4.
How To Enable TLS On Android Phone:
It is possible to enable TLS 1.2 on your Android phone if you have the latest version of the SDK. But you will need to have an Android version 4.1 or higher to do it. If your device is below this version, you need to upgrade to the latest one. You can get the latest version of the SDK from Google Play Services. But if you don’t want to update to the latest version, you can still use the workarounds provided below.
You should also make sure that you use a custom SSL socket factory instead of the default one. The default SSL socket factory is not compatible with TLS 1.2 so you need to create a custom one. The custom one should override all create Socket methods and callset Enabled Protocols(). The example code below demonstrates how to do it. It is important that you use the latest version of the SDK.
How To Affects Usability Of Shopping Carts:
The usability of shopping carts is a key consideration for mobile websites. This is because customers tend to abandon carts once they have added a product. When designing your shopping cart, consider the common problems that customers face. By following some guidelines, you can improve your customer experience and increase conversion rates. If you’re interested in improving the usability of shopping carts on mobile websites, take some time to learn about user experience.
The checkout process is one of the major causes of cart abandonment. While this happens across all platforms, it’s particularly noticeable on mobile. Many e-commerce sites implement a one-page checkout that lets users view all necessary information without having to switch pages. But it’s impossible to recreate this experience on mobile because the checkout form is broken up into multiple pages. Despite the obvious inconveniences, mobile users often abandon carts at the checkout page, and abandon the cart in frustration.
How To Prevents Man-In-The-Middle Attacks:
A Man-in-the-Middle attack is a type of cyberattack in which the attacker intercepts data transfers between the client and the server. The attacker can also intercept and manipulate future transactions by inserting false information into the transfer. A common example of this is when a hacker sets up a fake chat service claiming to be a reputable bank. The hacker then can use that information to transfer funds to a different account.
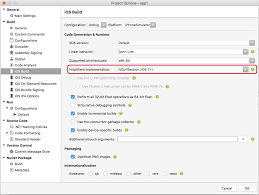
Open Google Chrome:
- Open Google Chrome.
- Tap Alt-F and select Settings.
- Scroll down and select Show advanced settings…
- Under Network, click Change proxy settings…
- Select the “Advanced” tab.
- Under Security, find and check Use TLS 1.1 and TLS 1.2.
- Click the OK button.
A Man-in-the-Middle attack is a type of eavesdropping attack that occurs when an attacker intercepts a conversation or data transfer and registers themselves as a legitimate party. It is not always possible for users to identify a malicious actor, which is why it’s critical to protect your data from Man-in-the-Middle attacks. To prevent these attacks, make sure your communication uses standardized protocols, such as HTTPS, strong WEP/WAP encryption, and strong router login credentials.


