How Do I Allow SSH Traffic Into My Home Network?
Allow SSH Traffic is a protocol that ensures data sent across the network is unaltered. Its main functions are encryption and authentication.
It uses a client-server architecture model and is used to transfer files between a host computer (the client) and another host server. It also allows for remote access to servers behind firewalls.
SSH, or Secure Shell, is a vital tool for secure remote access to servers and other computing devices. It allows you to establish encrypted connections, ensuring the confidentiality and integrity of data transmitted during remote sessions. However, by default, SSH traffic is not always allowed, requiring specific configuration on your system or network. This guide delves into the various methods for enabling SSH traffic, catering to different operating systems and network environments.
Understanding the Landscape:
Before diving into specific steps, it’s crucial to grasp the context in which you’re enabling SSH traffic. Here are some key considerations:
- Operating System: The process for enabling SSH traffic varies depending on your operating system (e.g., Linux, Windows, macOS).
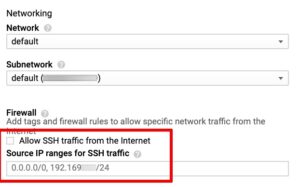
- Firewall: Most systems have a built-in firewall that filters incoming and outgoing traffic. You’ll need to configure the firewall to allow SSH connections.
- Network Environment: If your device is part of a larger network with additional security measures (e.g., security groups in cloud environments), you might need to adjust settings at the network level.
Enabling SSH Traffic on Different Operating Systems:
1. Linux:
- Starting and Enabling the SSH service:
- Use the following command to check if the SSH service is running:
sudo systemctl status ssh - If it’s not running, start it using:
sudo systemctl start ssh - To enable the service to start automatically on boot, use:
sudo systemctl enable ssh
- Use the following command to check if the SSH service is running:
- Configuring Firewall Rules:
- Use tools like
iptablesorfirewalldto create rules allowing SSH traffic. Here’s an example usingiptables:sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT - This rule allows incoming TCP traffic on port 22 (default SSH port) to be accepted.
- Use tools like
2. Windows:
- Enabling OpenSSH Server:
- Open the “Turn Windows features on or off” window.
- Locate “OpenSSH Server” and check the box to enable it.
- Click “OK” and restart your computer.
- Configuring Firewall Rules:
- Open Windows Security and navigate to “Firewall & network protection.”
- Click “Allow an app through firewall.”
- Click “Change settings” and then “Allow another app.”
- Browse to the OpenSSH executable (usually
C:\ProgramData\ssh\sshd.exe) and add it. - Select “TCP” and enter the port number (default is 22).
- Click “Add” and then “OK” to save the changes.
3. macOS:
- Starting and Enabling SSH:
- Open “System Preferences” and navigate to “Sharing.”
- Select “Remote Login” and check the box next to “SSH.”
- You can also configure options like allowed users and port number.
Additional Considerations:
- Security Best Practices:
- While enabling SSH traffic is essential for remote access, it’s crucial to prioritize security. Here are some recommendations:
- Use strong passwords or SSH keys for authentication.
- Restrict access to specific IP addresses or users.
- Keep your SSH server software up-to-date with security patches.
- Monitor your system for suspicious activity.
- While enabling SSH traffic is essential for remote access, it’s crucial to prioritize security. Here are some recommendations:
- Advanced Configurations:
- The provided examples offer basic guidance. For more advanced configurations, refer to the official documentation for your specific operating system and firewall tools.
- Network Security Groups:
- If your device resides in a cloud environment or managed network, you might need to adjust security group rules to allow SSH traffic. Consult your network administrator for specific instructions.
Security
The Secure Shell protocol (SSH) provides several benefits for remote system management, file copying and other network tasks. While it presents some security threats, these are mitigated by a variety of tools and best practices.
To enhance security, you can use firewall rules to block unauthorized traffic from accessing your SSH server. You can also change the default port to reduce the likelihood of brute force attacks and unauthorized login attempts. To do this, edit /etc/ssh/sshd_config to set the listen address on which the sshd service should be listening.
You can also prevent attacks by creating a list of banned IP addresses. This can be done using Fail2ban and other similar tools. This helps to limit incoming connections from IP addresses that have been blocked multiple times. You should also disable password authentication and restrict root logins to specific users. This will further decrease the number of potential entry points for attackers. You can also create network segments based on functions and apply strict firewall rules.
Port forwarding
Port forwarding allows data to be forwarded from a local computer to a remote server over an encrypted SSH connection. It’s a useful tool for system administrators and others who need secure remote access to network services.
To configure port forwarding, open the SSHD configuration file /etc/ssh/sshd_config and find the Gateway Ports directive. This setting determines which ports will be forwarded through the SSH tunnel to the managed device. You’ll need admin privileges to view or edit this setting.
To use dynamic forwarding, start an SSH session with the -D option and a chosen local port number (e.g., 1080). The SSH client then creates a SOCKS proxy on this local port and routes Internet traffic through it to the managed device. Each program that needs to connect to the remote server must be configured to use this SOCKS proxy. This is especially important for users behind a corporate firewall. It enables them to bypass the firewall and reach websites and other applications that would otherwise be blocked.
UPnP
UPnP can be very convenient, but it opens your network to online threats. Leaving it on will make it easier to open ports for devices on your network or for online games, but it can also allow hackers to establish infections in your system that will withstand your firewall policies and allow them to recurrently connect from the internet.
The problem is that UPnP doesn’t use authentication or authorization to discover devices on the network, and it assumes that all devices are trusted and local. This allows hackers to find a backdoor in your router that can remain undetected for months – giving cyber attackers the time they need to do serious damage.
To disable UPnP on your router, configure it to not accept incoming connections on ports mapped with UPnP. To do this, login to your router’s configuration interface and look for options like Zero-configuration networking or UPnP server. If you’re using Kerio Control, you can enable this feature by navigating to Configuration > Security Settings > UPnP Server.
Routers
Whether you want to stop Allow SSH Traffic into the router itself, or into one machine on your home network, you need to check the configuration of the router. Check to see if you’ve changed any port forwards or put machines in the DMZ. If you haven’t, you should be fine.
Using SOCKS to tunnel SSH, network traffic sent out from the local system is redirected to an SSH connection with a jump server. The jump server then encapsulates the packets for forwarding. This allows SSH to manage application ports, rather than relying on the well-known ports used for specific network applications.
Ensure that you have enabled authentication for your router Carter before adding SSH. This can be a local username and password or an authentication, authorization and accounting (AAA) server running TACACS+ or RADIUS. The router will use a vty resource for this connection, which by default is Telnet.
Conclusion:
Enabling SSH traffic opens doors for secure remote access but necessitates careful consideration of security implications. By following these guidelines and adhering to best practices, you can establish a secure connection while maintaining control over your system’s accessibility. Remember, staying informed about security updates and implementing appropriate measures is crucial for safeguarding your system against potential threats.

Leave a Reply