How Do I Enable SMB Signing in Group Policy Management
SMB signing can be enabled with Group Policy Management. Enabling SMB signing is necessary because unsigned SMB packets can be intercepted by attackers after gaining access to the network. This allows them to modify unsigned packets and gain access to data. Unsigned SMB packets can also be used to perform session hijacking, which means that an attacker will pretend to be a server or client device and hijack the authentication session, which is necessary to obtain access to data. Enable SMB Signing In Group Policy.
SMB 1.0 is no longer considered safe, and most security experts recommend disabling this protocol. This protocol was created in the 1980s and was first implemented in the Windows operating system in 1992. Many people still use it, despite the fact that there are safer and more secure options. The best way to make sure your network is secure is to use HTTPS Google.
SMB is a standard for file access and communication between computer processes and devices. Although some current editions of Windows still support SMBv1, Microsoft has decided to remove the SMBv1 binaries from future versions of the operating system. As a result, Windows server and client editions will not include the necessary drivers and DLL files to support SMBv1. When this happens, any connection requiring SMBv1 will fail.
How To Configuring SMB Signing In Group Policy:
The original SMB version, SMBv1, was introduced in the late 1980s and has gone through several iterations. Windows 95 introduced CIFS as a replacement for SMBv1. However, SMBv1 is not safe for use in modern applications. The lack of encryption has made it vulnerable to attacks such as Wanna Cry and Not Peaty. It’s also inefficient, causing congestion and reducing performance.
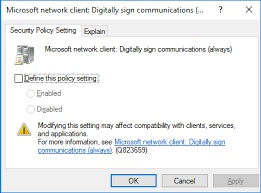
The configuration of SMB signing can be performed on domain controllers, clients, or domain members using Group Policy. In the “Security Options” section of Group Policy, you can change whether all SMB traffic should be signed. Note that this method uses extra processing and can reduce SMB performance. Therefore, it is recommended to use the “Digitally sign communications (always)” group policy to enable SMB signing on your domain or client computers. In addition, you can also set a registry setting called “Require Security Signature” to require SMB signing on your domain controllers and clients.
How To SMB 1.0 Is No Longer Considered Safe:
Using SMB signing is a good way to secure your network. SMB signing allows you to make sure that only your trusted systems can access your network. This prevents man-in-the-middle attacks. It also authenticates SMB sessions at the packet level.
SMB signing is a way to secure your network by ensuring that the traffic that goes through it is signed by a trusted entity. This can be accomplished through a Group Policy setting or by changing a registry key. If you need to enable SMB signing, read the interoperability matrix for SMB signing for more information.
How To Require Security Signature Registry Key:
There are two ways to enable SMB signing in Windows. The easiest way is to use Group Policy. You can also use the registry settings to turn on the feature. In either case, make sure that the SMB1 client is updated and the server is patched.
SMB signing adds security to the SMB protocol. It helps prevent man-in-the-middle attacks by verifying the integrity of each packet sent and received by the servers and clients. It also protects against protocol downgrade attacks.
How To Lanman Server Service:
In order to allow SMB sharing, you need to enable the Lanman Server service on your computer. This service is used to manage the default shares on your computer. Disabling this service will prevent other computers from accessing these shares. However, it will not prevent you from using the internet or using other network devices.
The Lanman Server service is a part of the workgroup and domain network. If you disable this service, you will give your administrators a lot of headaches in the future. You can use CIFS or another open-source implementation of the SMB protocol, such as Samba, which is commonly used in Linux and macOS. Another implementation is NQ, which was developed by Visuality Systems.
Go To Settings:
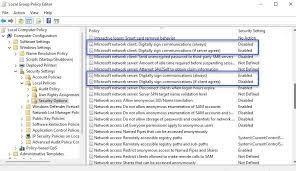
- SMB signing can also be enabled from the ’Local Group Policy Editor’ graphical application.
- In the app, go to Computer > Windows Settings > Local Policies > Security Options.
- Then change the policy value below to Enabled.
- Then the system needs to be restarted.
Enabling SMB signing in group policy helps secure your network. When SMB packets are sent through your network without being signed, an attacker can intercept and modify them. This allows them to perform a number of attacks, including session hijacking. These attacks can mimic legitimate authentication sessions or server devices. They can then gain access to your data.

Leave a Reply