How to Enable Mac on SSH
To enable SSH on Mac, follow these simple steps: Enable SSH on your Mac using the command line. Advanced users can also enable SSH using the System Preferences panel or Terminal. Once enabled, your Mac will be an active SSH server and ready to receive inbound connections.
To configure SSH on your Mac, you need to enable the SSH server and set up Remote Login. You will need audio or administrator privileges to run this command. After you enable SSH on your Mac, you will need to set a password for the user you will be connecting as. Once you’ve entered the password, you should be able to connect to the server using the command line Google.
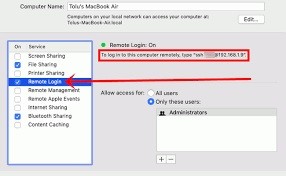
Modern Macs includes a built-in SSH server. To enable it, go to System Preferences, and enable the option. Select “All Users” as the default option, but you can customize the list of users to enable SSH.
How To Protecting Your Mac Against Unauthorized Logins:
SSH is a protocol that is used to connect to the network of your Mac. By default, macOS does not encrypt data sent over it. But there are several ways to protect your Mac from unauthorized logins. First, make sure you set up a separate user account and password for it. This will prevent other users from using your Mac and viewing your files. Another way to protect your files is to enable File Vault encryption. This feature will require a login password for you to access your private files.
If a brute force attack cannot find a valid account, it will be much harder to find one. If the attacker doesn’t have a valid login, he has to multiply the number of login attempts per second by the number of possible user names. This gives the system more time to reject an IP.
How To Authenticating A Client Using An SSH Key:
SSH key-based authentication is an alternative to password-based authentication. This method relies on the public and private keys of a client to identify them. The use of these keys is not governed by a central authority. The parties to a transaction to generate these keys.
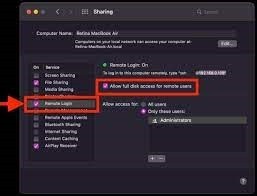
When SSH keys are shared, the public and private keys are encrypted with a passphrase and kept confidential on the client machine. It is important to protect the private key, because if it is compromised, an attacker could log into a server without authentication. The private key should be stored securely on a disk, preferably encrypted using a password, but the associated public key may be freely shared. Authenticating a client using an SSS key is a common practice in the internet today.
How To Creating A Custom Name For Mac On SSH:
The process of authenticating a client using an SSH key is quite simple. First, the client uploads its public key to the remote server and adds it to its authorized key list. The server then tests the private key to verify ownership. If the private key matches the public key, then the server will grant authentication.
SSH on macOS has a feature that lets you create a custom name for your Mac. By default, your SSH key pair will be id_is, but you can change this by setting a custom name in the users ssh file. However, you should know that you must make sure that your custom name is known by the SSH client.
How To Restricting SSH Logins To Certain Users Or Groups Of Users:
Restricting SSH logins to certain individuals or groups of users is an important security measure to prevent password-guessing attacks and SSH attacks on system accounts. There are a number of ways to achieve this. One common method is to modify the /etc/pam.d/sshd file to require “daemon-style style” login control and to set the Allow Groups attribute to “false”. In this way, only certain users or groups will be able to access a system account.
Open Check Settings:
- To find the SSH command you want to use to log in to your Mac from another computer, choose Apple menu > System Preferences, click Sharing, then choose Remote Login.
- The SSH command is displayed under the “Remote Login:
- Enabled” indicator.
- Enabling remote login to your Mac can make it less secure.
- See Mac security settings.
Another way to restrict SSH logins to specific users is to set the Deny Users and Allow Groups directives. You must reload SSH after you make changes to the Deny Users and Allow Group options.

Leave a Reply