How Do I Turn on Port 22
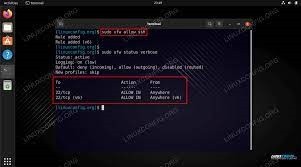
You can check to see if port 22 is open with a netstat command. Generally, this port is used for SSH servers. However, you should be aware of the cyber threats that exist in this port. To keep your system safe from cyber threats, you should configure outbound SSH in your firewall so that all connections to your network go to port 22.
Hackers use SSH port 22 as a way to probe your server for vulnerable software. They try dictionary and brute force combinations to get in, which can place an enormous load on your server. To avoid this, you should place your SSHd on another port. This way, you’ll fool the attackers and keep them from using this port Google.
One of the most common attacks targets using SSH port 22 is an exploit involving a vulnerability in the OpenSSH protocol. A vulnerability in this protocol allows an attacker to access a server’s internal networks. An attacker could also access your internal network by stealing your SSH password.
How To SSH Client And Sftp Programs Support -P Port> Option:
Another vulnerability affecting SSH port 22 is a Man-in-the-Middle attack, which allows an attacker to modify the content of messages or strings sent between the server and the client. The exploit relies on the fact that the SSH version chosen by the client differs from the crypto algorithms used by the server.
SFTP, which stands for Secure File Transfer Protocol, uses SSH protocol to transfer files and other data over a Secure and Encrypted Connection. Unlike FTP, which uses an insecure connection, SFTP uses an encrypted connection and supports multiple authentication methods. It works in a client-server architecture and enables a client to upload and download files or manipulate directories on a server. SFTP uses the default SSH port 22, making it easy to manage network rules.
How To SSH Port 22 Is Vulnerable To Cyber Threats:
SFTP also allows users to use SSH private keys. This adds an extra layer of security to the authentication process. This option is useful if you want to restrict access to certain types of files, or you want to control access to a specific user.
Command-line options are available on most operating systems. Linux, for example, includes built-in SFTP and FTP programs. However, if you’re not comfortable using Linux command-line programs, you can also use PuTTY, which is a free SFTP client that enables secure SSH connections to Unix Timesharing Service servers. There are several other commercial and open-source packages available.
How To Open Firewall Ports In Windows 10:
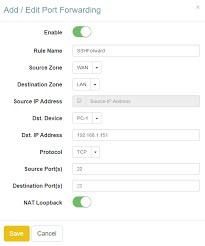
Configuring outbound SSH in a network firewall is one of the easiest ways to allow remote connections. By forwarding all connections to port 22, you allow SSH connections to connect from anywhere. For more information, see “SSH – Configure outbound SSH in a firewall” for details.
SSH has many uses, including remote access by developers and system administrators. In these cases, configuring outbound SSH in a firewall allows remote access through a tunnel. The firewall can then forward all port 22 traffic to your internal network or to the DMZ. You can also configure different ports for different servers to enable SSH access. Depending on the server, you may need to configure a VPN for SSH. Most VPNs use the IPsec protocol for this purpose. Alternatively, you can use Iptables, a host firewall built into the Linux kernel, to block or permit access to certain ports.
Configure The Windows Firewall:
- Click Start –> Control Panel –> Windows Firewall –> Exceptions tab.
- Click the Add Port… button.
- Name: SSH.
- Port number: 22.
- TCP.
- Click OK to add the SSH exception to the firewall.
- Click OK to close the Windows Firewall screen.
To configure outbound SSH in a firewall, create a rule for TCP port 22 and enable tunneling. You can also restrict access to external cloud servers by using a jump server. It is important to note that unrestricted outbound SSH can be risky. It can be dangerous to leave connections unrestricted, since unrestricted access can result in a high risk of data breach. Nevertheless, it is still recommended to limit access to outbound SSH.

Leave a Reply