How to Enable SSL 3.0 in Chrome
In order to enable SSL 3.0 in chrome on your browser, you must first enable TLS 1.2. If you are using SSL 2.0, you must disable it. And if you want to use SSL 3.0, you must disable TLS 2.0 first. To do so, follow these steps.
To make your website secure and increase the speed of your website, you can enable TLS 1.3. TLS 1.3 offers advanced features like stateless resumption and forward secrecy. They also eliminate roundtrip latency and reduce computational overhead for repeat visitors Google.
HTTPS uses block ciphers, which are known to have security issues. The newer TLS 1.3 replaces block ciphers. Block ciphers encrypt data in fixed-length blocks, which may need padding. By contrast, stream ciphers use pseudo-random streams.
How To TLS 1.3 Performance And Security:
TLS 1.3 isn’t perfect, but it’s still a step in the right direction. The modern trend in web security is towards client-side security, as clients are far more vulnerable and easier to compromise. As a result, TLS is an important part of the security of browsers.
Google Chrome offers several security features for its users, including TLS 1.3. It is a draft working version of the encryption protocol that was released in 2017. Many websites and cloud services have begun to support this security protocol. You can enable TLS 1.3 in Chrome starting with version 63. To enable the feature, open the Chrome preferences and double-click on the tls13-variant entry. Modify the value to 4 to enable TLS 1.3.
How To TLS 1.3 Features:
This new protocol offers better security for websites that store sensitive information. It aims to make less information available in plain text by using three cipher suites. TLS 1.2 exposes the identity of the client, but TLS 1.3 makes this information confidential. Once TLS 1.3 is implemented, servers and applications will need to implement it. Although the new version is a significant upgrade from TLS 1.2, Chrome users will not notice a noticeable difference.
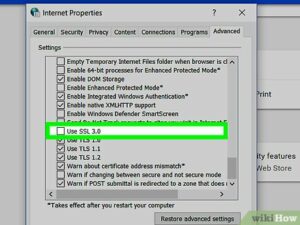
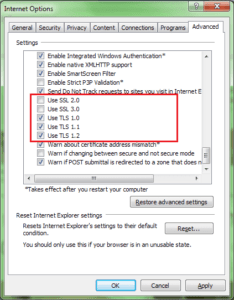
There are a few different ways to enable TLS v3 ciphers in Chrome. First, you can choose to use SSL 2.0 or TLS 1.1. Make sure to uncheck the Use TLS 1.0 option. If you have a proxy set up on your Windows computer, you can use this to enable SSL v3.
How To TLS V3 Ciphers:
While TLS 1.1 is still widely used, many websites are using TLS v3. TLS is a cryptographic protocol that allows websites to encrypt and decrypt communications across a network. It also helps websites to ensure privacy and data integrity.
In order to make your website secure, you should make sure that your server is running TLS v3. You should also disable RC4 on your servers to protect yourself from attacks. In addition, you should remove the support for older versions of TLS 1.1 and TLS 1.0. This will make it harder for stragglers to exploit your website.
How To Disabling SSL V3:
If you want to stop using SSL v3 in Chrome, you’ll need to disable it in its security settings. This is a feature that Chrome doesn’t include by default. You can disable it in the advanced tab, where you’ll also find the TLS 1.0 and 1.1.
The move is in response to a serious security vulnerability that Google recently disclosed. The flaw, dubbed POODLE (Padding Oracle on Downgraded Legacy Encryption), allows an attacker to decrypt encrypted traffic, including cookies. SSL v3 was developed in the mid-90s and supports outdated cipher suites. This makes it insecure from a cryptographic perspective, and Google plans to stop supporting it in Chrome in the next two months.
Click On Settings:
- Start Google Chrome.
- Click on the “Wrench” icon and then click on “Options”.
- Scroll down until you see “Network” and then click “Change proxy settings.”
- Click on the “Advanced” tab; scroll down until you see “Security”.
- Check the “Use SSL 3.0” box, then click “OK” to enable SSL 3.0 in Google Chrome.
Chrome 39 will disable SSLv3 fallback by default. This feature will only be needed if SSLv3 servers are buggy. If your server supports TLS 1.0, you can continue to use them. But if your server doesn’t support TLS 1.0, you’ll have to use HTTPS instead.

Leave a Reply